Comparison of the distroless alpine image vs the standard alpine image
With GoReleaser and Trivy
Table of contents
Introduction
In this article, I compare the creation of the container image for my project mineclt 🗺. I use GoReleaser
To create a container image with the help of GoReleaser we need to add the following part to the goreleaser.yaml configuration file:
dockers:
- image_templates: [ "ghcr.io/dirien/{{ .ProjectName }}:{{ .Version }}-amd64" ]
dockerfile: Dockerfile
use: buildx
build_flag_templates:
- --platform=linux/amd64
- --label=org.opencontainers.image.licenses=Apache-2.0
- ... additional labels
Afterwards we create a Dockerfile in the root of the project folder:
FROM ...
COPY minectl \
/usr/bin/minectl
ENTRYPOINT ["/usr/bin/minectl"]
GoReleaser Trivia: We are not building any go files in the Docker build phase, we are only copying the existing binary to the base image and set the
ENTRYPOINT
Now we can run execute the goreleaser release with the following command.
goreleaser release --snapshot --skip-sign --rm-dist
After the release is created, we can then compare the size and vulnerabilities of both images. To scan the images, I am going to use OSS security tool Trivy.
distroless/alpine-base
The distroless project aims to provide minimal image without a shell or package managers and provide SBOM support and signatures for known provenance and more secure base images.
We will use the distroless/alpine-base image (ghcr.io/distroless/alpine-base@sha256:6b798ef68d029c2311e461b1dfdedfbb8cff4784a31088811960d23745336caf) as base image in the Dockerfile.
trivy image ghcr.io/dirien/minectl:v0.23.0-SNAPSHOT-amd64
2022-08-19T12:24:49.880+0200 INFO Need to update DB
2022-08-19T12:24:49.880+0200 INFO DB Repository: ghcr.io/aquasecurity/trivy-db
2022-08-19T12:24:49.880+0200 INFO Downloading DB...
33.66 MiB / 33.66 MiB [-------------------------------------------------------------------------------------------------------------------------------------------------] 100.00% 979.91 KiB p/s 35s
2022-08-19T12:25:27.427+0200 INFO Vulnerability scanning is enabled
2022-08-19T12:25:27.427+0200 INFO Secret scanning is enabled
2022-08-19T12:25:27.427+0200 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
2022-08-19T12:25:27.427+0200 INFO Please see also https://aquasecurity.github.io/trivy/v0.31.0/docs/secret/scanning/#recommendation for faster secret detection
2022-08-19T12:25:28.833+0200 INFO Detected OS: alpine
2022-08-19T12:25:28.833+0200 INFO Detecting Alpine vulnerabilities...
2022-08-19T12:25:28.834+0200 INFO Number of language-specific files: 1
2022-08-19T12:25:28.834+0200 INFO Detecting gobinary vulnerabilities...
ghcr.io/dirien/minectl:v0.23.0-SNAPSHOT-amd64 (alpine 3.16)
Total: 0 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 0)
usr/bin/minectl (gobinary)
Total: 2 (UNKNOWN: 1, LOW: 0, MEDIUM: 0, HIGH: 1, CRITICAL: 0)
┌─────────────────────────────────────┬─────────────────────┬──────────┬───────────────────┬───────────────┬─────────────────────────────────────────────────────────────┐
│ Library │ Vulnerability │ Severity │ Installed Version │ Fixed Version │ Title │
├─────────────────────────────────────┼─────────────────────┼──────────┼───────────────────┼───────────────┼─────────────────────────────────────────────────────────────┤
│ github.com/prometheus/client_golang │ CVE-2022-21698 │ HIGH │ v1.11.0 │ 1.11.1 │ prometheus/client_golang: Denial of service using │
│ │ │ │ │ │ InstrumentHandlerCounter │
│ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-21698 │
│ ├─────────────────────┼──────────┤ │ ├─────────────────────────────────────────────────────────────┤
│ │ GHSA-cg3q-j54f-5p7p │ UNKNOWN │ │ │ The Prometheus client_golang HTTP server is vulnerable to a │
│ │ │ │ │ │ denial of │
│ │ │ │ │ │ service attack... │
│ │ │ │ │ │ https://github.com/advisories/GHSA-cg3q-j54f-5p7p │
└─────────────────────────────────────┴─────────────────────┴──────────┴───────────────────┴───────────────┴─────────────────────────────────────────────────────────────┘
Check the image size:
❯ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
ghcr.io/dirien/minectl v0.23.0-SNAPSHOT-arm64 7dd5e274c34a 13 seconds ago 78.2MB
ghcr.io/dirien/minectl v0.23.0-SNAPSHOT-amd64 0c28ff0969ab 17 seconds ago 81.6MB
Le us check the layers with the help of dive. We can see that the base image of distroless is slightly larger than the one from alpine
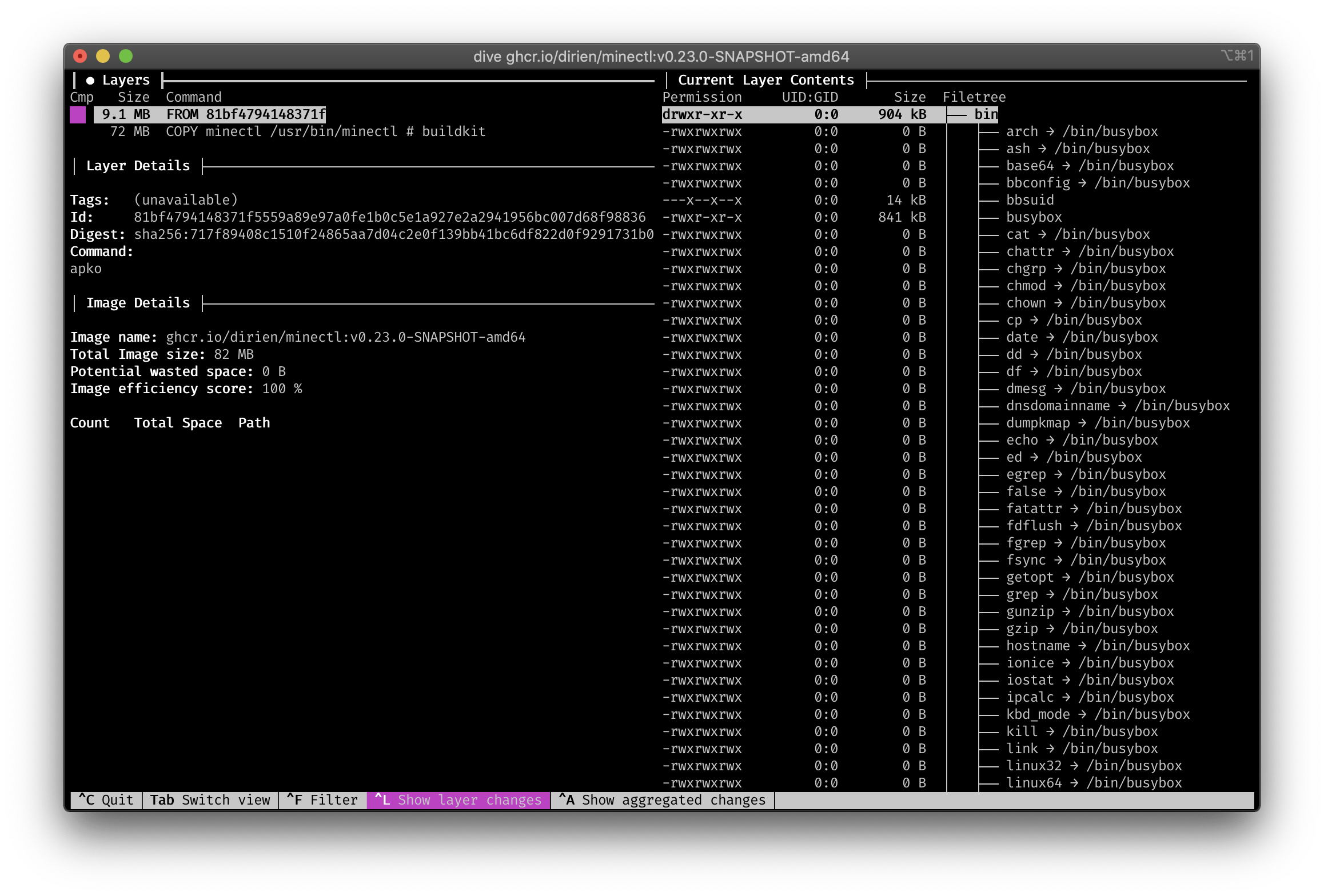
Strangly I could still use the shell and apk in the distroless image. Maybe I did something wrong here?
❯ docker run --entrypoint sh -it ghcr.io/dirien/minectl:v0.23.0-SNAPSHOT-amd64 / # apk apk-tools 2.12.9, compiled for x86_64.
alpine
I use here the official Alpine Linux Docker image with a whooping size of 5MB.
We use the alpine:3.16.2 image (alpine@sha256:bc41182d7ef5ffc53a40b044e725193bc10142a1243f395ee852a8d9730fc2ad) as base image in the Dockerfile
trivy image ghcr.io/dirien/minectl:v0.23.0-SNAPSHOT-amd64
2022-08-19T12:35:23.813+0200 INFO Vulnerability scanning is enabled
2022-08-19T12:35:23.813+0200 INFO Secret scanning is enabled
2022-08-19T12:35:23.813+0200 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
2022-08-19T12:35:23.813+0200 INFO Please see also https://aquasecurity.github.io/trivy/v0.31.0/docs/secret/scanning/#recommendation for faster secret detection
2022-08-19T12:35:25.072+0200 INFO Detected OS: alpine
2022-08-19T12:35:25.072+0200 INFO Detecting Alpine vulnerabilities...
2022-08-19T12:35:25.072+0200 INFO Number of language-specific files: 1
2022-08-19T12:35:25.072+0200 INFO Detecting gobinary vulnerabilities...
ghcr.io/dirien/minectl:v0.23.0-SNAPSHOT-amd64 (alpine 3.16.2)
Total: 0 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 0)
usr/bin/minectl (gobinary)
Total: 2 (UNKNOWN: 1, LOW: 0, MEDIUM: 0, HIGH: 1, CRITICAL: 0)
┌─────────────────────────────────────┬─────────────────────┬──────────┬───────────────────┬───────────────┬─────────────────────────────────────────────────────────────┐
│ Library │ Vulnerability │ Severity │ Installed Version │ Fixed Version │ Title │
├─────────────────────────────────────┼─────────────────────┼──────────┼───────────────────┼───────────────┼─────────────────────────────────────────────────────────────┤
│ github.com/prometheus/client_golang │ CVE-2022-21698 │ HIGH │ v1.11.0 │ 1.11.1 │ prometheus/client_golang: Denial of service using │
│ │ │ │ │ │ InstrumentHandlerCounter │
│ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-21698 │
│ ├─────────────────────┼──────────┤ │ ├─────────────────────────────────────────────────────────────┤
│ │ GHSA-cg3q-j54f-5p7p │ UNKNOWN │ │ │ The Prometheus client_golang HTTP server is vulnerable to a │
│ │ │ │ │ │ denial of │
│ │ │ │ │ │ service attack... │
│ │ │ │ │ │ https://github.com/advisories/GHSA-cg3q-j54f-5p7p │
└─────────────────────────────────────┴─────────────────────┴──────────┴───────────────────┴───────────────┴─────────────────────────────────────────────────────────────┘
Check the image size:
❯ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
ghcr.io/dirien/minectl v0.23.0-SNAPSHOT-arm64 74fe045a62a9 2 minutes ago 74.8MB
ghcr.io/dirien/minectl v0.23.0-SNAPSHOT-amd64 e5986e55995b 2 minutes ago 78MB
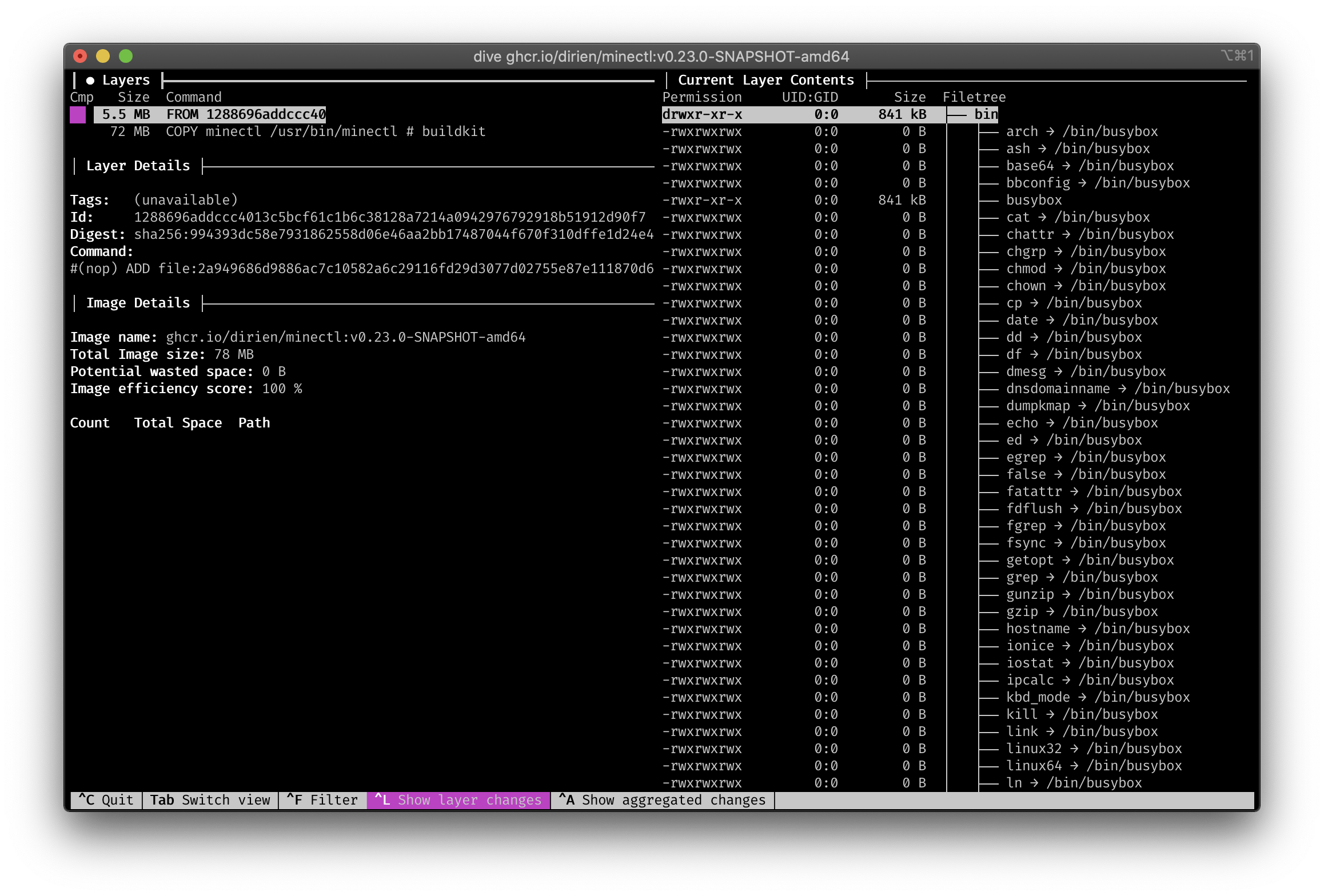
And take a look with dive
Conclusion
As we could see, there is no difference in the amount of vulnerabilities Triviy found and the slightly larger image size with distroless is negligible.
For my personal projects I will switch to the distroless project, as I really like that they use apko and melange to create the base images and SBOM support and signatures is already active and in use!